By Patrick J. Chaisson
Nothing seemed to work. The Allied codebreakers tried every possible trick and combination, but these new ciphers defied all attempts at decryption. On February 1, 1942, British analysts discovered they could no longer read intercepted radio communications between German U-boat captains and their commanding officer, Vice Admiral Karl Dönitz. Overnight, a vital part of the United Kingdom’s super-secret cryptanalytic program—Ultra—had been plunged into darkness.
This intelligence blackout could not have come at a worse time for the Allies. Already, a handful of aggressive Nazi submarines were wreaking havoc all along North American shipping lanes. Dönitz’s Operation Drumbeat would result in 216 merchantmen sunk off the U.S. East Coast during the first three months of 1942 alone. American countermeasures all proved hopelessly inadequate.
Something needed to be done about Admiral Dönitz’s deadly underwater predators before they completely choked off the supplies of food, munitions, and fuel needed to keep Britain in the war. It was a daunting task; defeating the U-boats meant conducting a maximum coordinated effort among the air, sea, and intelligence services of two distrustful allies. Could the United Kingdom and the United States put aside their suspicions and join in a common endeavor to penetrate the enemy’s new communications procedures?
During the 1920s and 1930s, Germany developed a portable, easy-to-operate cipher machine known by its brand name Enigma. All three branches of Hitler’s armed services utilized it to encrypt tactical communications throughout World War II. Many German civil agencies also adopted this mechanism; as a result, hundreds of thousands were built.
Weighing 23 pounds, the device resembled an oversized typewriter with a miniature telephone switchboard on its surface. Electrically powered, it also featured a 26-character light panel. Three (later four) cylindrical metal rotors fit inside a basket behind the light panel. Each rotor contained a distinct web of wiring contacts and had to be loaded into the basket in a specific order. The Enigma came with five differently wired rotors, although by 1940 those on Dönitz’s U-boats started carrying eight for additional security.

An instruction sheet called the key list told code clerks which rotors to use on any given day (operators routinely changed their settings at midnight). This list also prescribed how to arrange the rotors, to include a moveable placement notch on the outer ring of every cylinder. Lastly, the key list provided daily configurations for Enigma’s plugboard, which the Germans termed a “stecker.”
To encrypt text, Enigma employed an innovative electromechanical character substitution process. Once the operator had his apparatus set up properly, he began by pressing a key. This sent an electrical impulse through the stecker, changing its path from one letter value to another. From there, the current passed across three or four rotors. Each rotor advanced once in turn, rerouting the electric signal several times before that impulse reached a reflecting plate. This plate diverted the current once again before returning it through the rotors and stecker. Finally, a letter would flash on the light panel, which the operator would then write down.
By entering content in this fashion, German code clerks could rapidly transform important military communications into a series of seemingly meaningless letters. Deciphering an encrypted message was as simple as typing those letters and noting what lit up on the lampboard providing the recipient had a correctly configured Enigma.
Its cryptographic power was staggering. According to mathematician Dan Fleisch, one three-rotor Enigma could generate a number of possible letter combinations equaling 10 to the 114th power—or more than the number of atoms in the known universe. A four-rotor version, like the type found on German U-boats starting in 1942, produced combinations exceeding 10 to the 145th power.
British intelligence expert Stuart Milner-Barry described the Nazis’ confidence in their capable new enciphering device: “The Germans regarded the Enigma as a perfectly secure machine, proof against cryptanalysts however talented and ingenious they may be.” Yet already a group of brilliant codebreakers was learning how to crack this supposedly invincible system.
Beginning in 1932, three theoreticians with the Polish Cipher Bureau developed a mathematical equation that approximated the wiring connections of an Enigma rotor. Meanwhile, French spies had obtained other cryptographic information from a German turncoat, which they passed on to the Poles. By 1938, Poland had succeeded in constructing a mechanism that could test 17,000 possible rotor settings to help decipher intercepted radio messages. Its designers called their creation a Bomba.
No one is sure how this name came about. One story says the Poles came up with the term “Bomba” in honor of an ice cream treat they all enjoyed.
In late July 1939, just before the Nazi invasion, these Polish cryptanalysts shared their intelligence breakthrough with French and British agencies. The Poles even sent along an operating replica of the Enigma. In the United Kingdom, a Polish-built Bomba made its way to Bletchley Park, Buckinghamshire, and into the possession of a highly classified facility there known as the Government Code and Cypher School (GC&CS).
Teams of mathematicians, engineers, linguists, and military intelligence officers at GC&CS studied with astonishment what their Polish and French colleagues had provided. The British now understood Enigma’s logical foundation; furthermore, they obtained several tools that one day might enable them to penetrate their foe’s sophisticated enciphering protocol. For the time being, however, it remained a mystery just beyond the Allies’ ability to solve.
In a collection of rude huts located behind Bletchley Park’s Victorian-era manor house, some of Britain’s brightest minds began examining the problem. Two young theoreticians named Alan Turing and Gordon Welchman formulated several techniques intended to rapidly decipher Enigma messages. Welchman focused on defeating the Germans’ stecker plugboard, his “diagonal board” test dramatically reducing the number of possible combinations any decryption system would need to examine.
Alan Turing drew up an electromechanical means of proving or disproving millions of possible rotor settings. Based on but logically distinct from the Polish Bomba, Turing’s design operated in conjunction with Welchman’s diagonal board to attack Enigma’s vulnerable daily key codes. An ingenious electrical engineer named Harold “Doc” Keen transformed Turing and Welchman’s drawings into a functioning mechanism; by August 1940, the first operational “Bombe” (somewhere along the line its name changed to the French spelling) was delivered to GC&CS.
The British Bombe was a masterwork of engineering. Standing 61/2feet tall, seven feet long, and two feet wide, each unit weighed one ton. More than 200 were constructed during the war years, put to use at Bletchley Park and in a number of outstations scattered across Great Britain.
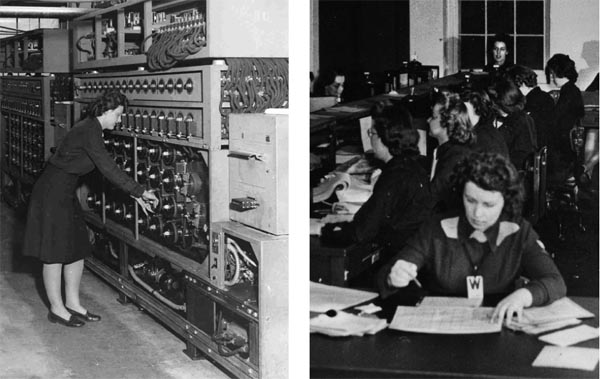
The Bombe operated like a series of Enigma machines in reverse. A series of 96 commutator wheels spinning at various speeds tested possible letter matches; if the Bombe found a “stop,” or possible solution, it would slow to a halt. An operator (often a Women’s Royal Naval Service member, or Wren) then rewound its commutators to where the Bombe stopped and wrote down that wheel position. Cryptanalysts tested this suspected key setting on a “checking device.” Whenever plain text emerged, they knew the day’s codes had been broken.
It should be remembered that the Bombe was only one part of an extraordinarily complicated system utilized by GC&CS to read enemy communications. Keys to this process were “cribs”—words or phrases likely to form a part of the intercepted message. A constant supply of good cribs was necessary to peer inside Enigma; obtaining these clues was equal part dogged persistence, inspired guesswork, and luck.
Fortunately for the Allies, German faith in Enigma’s security often led to procedural mistakes. These blunders, usually committed by lazy or bored operators, were quickly exploited by the talented analysts at Bletchley Park. One commander, for instance, invariably opened his daily reports with the salutation “Heil Hitler.” Famously, another code clerk used his girlfriend’s nickname—Cillie—for every message indicator he sent. These and other easily detectable patterns provided British codebreakers with many valuable cribs, starting points for their attacks into the foe’s ciphers.
Yet GC&CS’s most dangerous adversary was also its most security conscious. Unlike Germany’s army and air force, which could send messages by courier, teletype, or wire, the Kriegsmarine had no choice but to rely on radio communications. Admiral Dönitz regularly communicated with his U-boats via Morse code; from the war’s outset, Dönitz rightly suspected that Allied detection stations were listening in as he daily exchanged attack orders and situation reports with submarine captains operating across wide swaths of hostile ocean.
No one under Admiral Dönitz’s command got to choose his sweetheart’s name as an Enigma message indicator. Those settings were found in special codebooks known as Bigram tables, which also employed a second set of randomly generated letter pairs to doubly encrypt the initial rotor position for each message. Moreover, after February 1940, U-boats began utilizing eight rotors instead of the normal five as another layer of security.
All these precautions notwithstanding, for 18 months Bletchley Park experienced fair success in reading German naval radio traffic. Their efforts were aided immeasurably by the occasional capture of Kriegsmarine rotors, Bigram tables, and weather keys by the Royal Navy. In late 1941, for example, GC&CS knew Dönitz was about to issue new codes for his U-boats and even suspected the existence of a four-rotor Enigma.
When the Kriegsmarine switched to these updated ciphers and encryption machines in February 1942, Bletchley Park’s analysts knew they had been locked out of Enigma at a most inopportune time. Admiral Dönitz’s marauders were already killing hundreds of men and destroying tons of badly needed war matériel off the shores of North America. Raw United States naval and air forces could not combat this growing menace on their own. The British had vast experience in antisubmarine warfare, as well as the super-secret Ultra program, but how much were they willing to share with the Yanks?
Neither nation wanted to cooperate at first. “The World War II relationship between the British and American cryptanalysts began in confusion and mistrust,” observed historian Colin Burke. “The combination of British reluctance, America’s divided armed services, misunderstood agreements, and lost messages almost led to an end to the joint intelligence program.”
The U.S. Army and Navy maintained separate information gathering organizations, an arrangement that led to much wasted time and duplication of effort. Prior to Pearl Harbor, American codebreaking efforts focused on Japanese activity to the near exclusion of Germany. This was especially true of the U.S. Navy, whose communications intelligence division, OP-20-G, assigned a mere five analysts to work Enigma throughout most of 1941.
Although Prime Minister Winston Churchill and President Franklin D. Roosevelt pledged full cryptologic cooperation in mid-1940, the first U.S. visit to GC&CS took place almost nine months later. During February and March 1941, four American military intelligence officers toured the codebreaking facilities there. They came bearing gifts: copies of the “Purple” machine that decrypted Japanese diplomatic ciphers, as well as valuable data on Japan’s military codes.
In return, the Americans were shown a Bombe and given technical drawings of Germany’s Enigma. Bletchley Park also promised a Bombe would be sent on to the States as soon as one became available. This device was never provided; OP-20-G received blueprints in mid-1942 only after lodging a series of formal protests.
The American team chafed under their hosts’ security requirements, which included frequent warnings not to write down or discuss what they had seen with anyone not previously approved by GC&CS. And they were not allowed to see any operational data—kept hidden was such information as how Bletchley Park deciphered U-boat locations.
In fact, it was with extreme reluctance that Brigadier Stuart Menzies, head of British Intelligence, allowed the U.S. any access to Ultra’s secrets. He knew that if one word leaked, his opposite numbers in Germany would immediately change their ciphers and close the door on GC&CS’s invaluable cryptanalytic activities. Menzies also recognized that the United States, then a neutral power, was notoriously poor at keeping secrets, suggesting to Churchill in June 1941 that “the Americans are not in any sense as security minded as one would wish.”
Great Britain viewed the process of information sharing as a “need-to-know” matter. To preserve Ultra’s integrity, all decryption activities were to be performed in England and material deemed useful to U.S. forces sent by encrypted cable across the Atlantic. In no way did London want the Yanks to build their own Bombe. The risk of German agents finding out about it was just too great.
Yet, as horrified Americans watched torpedoed oil tankers burn just off their coastline, a rising clamor to stop the U-boats reached influential ears. In Washington, Chief of Naval Operations Admiral Ernest J. King demanded immediate action. His orders to the cryptanalysts of OP-20-G were both simple and direct: do whatever it takes to pierce these formidable new ciphers.
Navy researchers and scientists from the Massachusetts Institute of Technology (MIT) promptly set out to design an all-electric decryption device capable of defeating the four-rotor Enigma. This was done against London’s wishes, but as the bloody spring of 1942 dragged on into summer GC&CS admitted it could make little progress against the Kriegsmarine’s new enciphering systems. Without a functional alternative of their own to offer, British intelligence chiefs had no choice but to let the United States move forward on a solution.
The theoreticians at MIT enjoyed a favorable working relationship with American industry, most notably the National Cash Register Company (NCR) of Dayton, Ohio. It was in Dayton that the Naval Computing Machine Laboratory (NCML) was established in March 1942. NCML took over NCR’s former night school, Building 26, where civilian and military workers set out to construct a U.S. Bombe.
Selected to lead this development team was NCR’s chief of electrical engineering, Joseph R. Desch. At age 34, Joe Desch had already distinguished himself by inventing miniature fast-counting vacuum tubes called thyratrons that would later form the basis for modern computer technology. Desch’s pedigree as a second-generation German-American, however, aroused considerable suspicion. He could not visit his German-born mother without permission and was constantly shadowed by plainclothes naval agents throughout the war.
So concerned was the Navy over Joseph Desch’s loyalty that it assigned him a “liaison officer” named Lt. Cmdr. Ralph I. Meader, who as an added security measure slept in the Desch family’s spare bedroom. Meader also administered the NCML’s rapidly expanding activities in Dayton, working with OP-20-G to ensure the uninterrupted flow of personnel, materials, and funding. Part of his job involved pressuring Building 26’s workforce to increase productivity. “Men are dying,” Meader would say, “and you’re responsible for their deaths if you don’t get the job done.”

There were many early setbacks. MIT’s all-electric concepts were soon deemed impractical, as they required computing capabilities that did not yet exist. Desch next drew up plans for an electromechanical Bombe, one inspired by Turing and Welchman’s version but that incorporated several improvements. In practice, a production American Bombe ran from two to six times faster than its British counterpart.
The project benefitted from a gradual warming of relations between OP-20-G and GC&SC starting in the summer of 1942. Alan Turing visited Dayton that December, noting with interest the Americans’ thyratron memory tubes but also expressing concerns over other aspects of their prototype. Joe Desch ignored Turing’s criticism of his automatic rewind feature but eventually followed the British mathematician’s recommendation to standardize on one size of commutator wheel.
This wheel, which replicated Enigma’s rotor, was easily the most labor intensive element of Desch’s design. One commutator required 104 precisely hand-wired contacts, and each Bombe ran 64 commutators. To meet initial production requirements, roughly 6,000 of these wheels had to be manufactured quickly, accurately, and by people who could keep their mouths shut.
In April 1943, the first of 600 smartly uniformed U.S. Navy WAVES (Women Accepted for Volunteer Emergency Service) began arriving in Dayton to assemble cryptanalytic Bombes. Together with 200 male sailors they toiled in shifts around the clock, soldering colored wires to commutators. For security’s sake, the WAVES never saw both sides of a wheel; nor were they allowed to enter any area other than their assigned workspace.
The activity in Building 26 had to be kept highly classified. “We were sworn to secrecy,” said former WAVE Adeline Sullivan, “and periodically reminded about the Espionage Act.” Another WAVE, Veronica Mackey, vividly recalled a Navy officer telling her, “If you talk about what goes on here, you’ll be shot.” Mackey was stunned by the man’s blunt warning. “He got our attention,” she later remarked.
At the beginning of every shift, hundreds of WAVES marched one mile from their quarters in Sugar Camp—a former NCR sales training facility—to Building 26. After presenting proper identification to shotgun-armed Marine guards, the women entered large rooms where, according to Ronnie Mackey, “They gave you a soldering iron and we would … wire those little wheels. And when you’d finish one they promptly brought you another one.”
None of the Dayton WAVES realized how much Joe Desch and the Navy relied on their attention to detail. Early test machines spun commutators around at a rate of nearly 1,800 revolutions per minute. The slightest imperfection might send wheels flying across the room and set progress back days or weeks. And there was always pressure from Washington and Lt. Cmdr. Meader: every day you waste, more men die.
Throughout the spring of 1943, Desch’s team struggled to produce a functional apparatus. Their two prototypes, nicknamed Adam and Eve, continually leaked oil from gearboxes and other moving parts. Each Bombe housed 10 miles of wire and more than a million soldered connections, a mechanical nightmare for those repairmen whose job it was to keep these temperamental devices operational.
The Americans kept at it. Shortly after noon on May 28, two Navy technicians, Machinists Mate First Class Phil Bochicchio and Radioman K.P. Cook, fed a “menu” of intercepted Enigma settings into Adam and started up their Bombe. The contraption whirred noisily for a while before abruptly shutting down in what appeared to be another malfunction. The sailors gaped in amazement when Adam suddenly clattered back to life, rewinding itself onto a suspected commutator position just as designed. They ran the same data through Eve, which produced an identical set of wheel settings.
Bochicchio and Cook presented their findings to Lt. Cmdr. Meader, who transmitted this information via secure line to OP-20-G in Washington. Analysts there ran the decrypted settings through a checking device, then announced, “Jackpot.” The four-rotor Enigma had been defeated.
The 1,000 civilians, WAVES, and servicemen working in Building 26 immediately began turning out production Bombes, which they nicknamed “Grey Elephants.” Each one measured seven feet tall, 10 feet long, and two feet deep, while weighing approximately 5,000 pounds. A total of 121 Bombes were eventually manufactured with most of them being shipped to the Naval Communications Annex in Washington, D.C. The first Bombe arrived there on September 12, 1943.
Some 285 of the WAVES who had helped build these powerful new decryption machines accompanied their Grey Elephants to the Naval Communications Annex as Bombe operators. The glamour of duty in exciting Washington, D.C., was counterbalanced by long hours spent inside a swelteringly hot, noisy work environment. Crowded living conditions, rotating shifts, and unceasing pressure to keep silent about what they were doing took a toll on these young women. Many WAVES carried their secrets to the grave.
Meanwhile, the wizards of Bletchley Park continued to make great strides against Germany’s new U-boat ciphers. They scored an enormous victory on October 30, 1942, when a boarding party off the destroyer HMS Petard managed to “pinch” several codebooks from badly damaged U-559 near Port Said, Egypt. This intelligence coup came at high cost, though. Two brave British sailors drowned when the doomed submarine unexpectedly sank with them still inside.
A British Bombe that could read four-rotor Enigma ciphers also entered service in late 1943. By then, however, Admiral Dönitz’s last great U-boat offensive had ended in utter defeat. Other technological marvels such as microwave radar, aerial homing torpedoes, and radio direction-finding receivers enabled Allied forces to deliver unrelenting attacks on Nazi Germany’s submarine fleet. The great armada that invaded Normandy on June 6, 1944, crossed the English Channel largely without fear of underwater attack—only a few Unterseeboote remained at sea by this point in the war.
There was still plenty of work for the U.S. Navy Bombes and the WAVES who ran them. Joe Desch’s design included a feature that allowed his machines to decipher three-rotor Enigma traffic, volumes of which were intercepted daily from the German Army and air force. GC&CS, now a fully British-American operation, asked OP-20-G to help reduce the backlog. Washington-based Bombe operators devoted approximately 45 percent of their processing time to decrypting these tactical messages; the rest of their efforts went toward fighting the U-boats.
Recently declassified reports credit the U.S. Bombes with breaking a total of 301,629 enemy messages. It may never be known how many of these jackpots resulted in actionable information. However, Ultra did figure in several American antisubmarine successes, including the spectacular capture of U-505 by sailors of Captain Dan Gallery’s Task Group 22.3 on June 4, 1944.
At war’s end, the feelings of suspicion and distrust that once existed among intelligence professionals from the United Kingdom and United States had been replaced by a spirit of genuine cooperation at all levels. Nowhere was this better illustrated than in the partnership that grew between GC&CS and OP-20-G. General Dwight D. Eisenhower, a man who understood much about the nature of coalition warfare, later remarked that the Allies’ ability to read Germany’s ciphers “saved thousands of British and American lives and, in no small way, contributed to the speed with which the enemy was routed and eventually forced to surrender.”
The international team of theoreticians, electrical engineers, and Navy WAVES who together defeated Enigma would wholeheartedly agree with Ike’s assessment.
A retired U.S. Army officer, Patrick J. Chaisson writes on a variety of World War II topics from his home in Scotia, New York.